Accellion's Trust Center
page suggests CVE patches for known vulnerabilities and their blog
suggests they are 100% compliant and yet 100% owned by adversaries. Why?
On SolarWinds'
Trust Center page, they have 100% compliance
— and yet were also 100% owned by adversaries. Why?
Do we really need more examples at this massive scale to finally come to terms that Compliance ≠
Security?
It used to be acceptable for security hygiene weaknesses like…
- code repos turning from private to public,
- not knowing when non-team members are making malicious modifications,
- not understanding if third-party software on all your critical processes is running the most recent security updates provided by your software vendor,
- not ensuring trusted third-party or open-source code components for your developed products,
- not adding additional security controls to prevent the access from unauthorized sources, and
- not automating threat pattern recognition by correlating historical tacking of combined scenarios observed over time
…to infect unsuspecting customers.
The Accellion and SolarWinds software cybersecurity attacks just changed everything.
Brief Introduction
The SolarWinds cyber breach was a pivotal moment for
software cybersecurity assurance, raising everyone’s awareness for the need of software supply chain integrity, proving that attackers can breach an organization through their trusted cybersecurity software vendors.
"This incident has historical significance. It is a shift in the tectonic plates of cybersecurity....and warrants a review of our existing policy. Traditional cybersecurity teams and traditional IT teams don't recognize it."
—
Jim Routh, CISO, MassMutual (Interos Webinar)
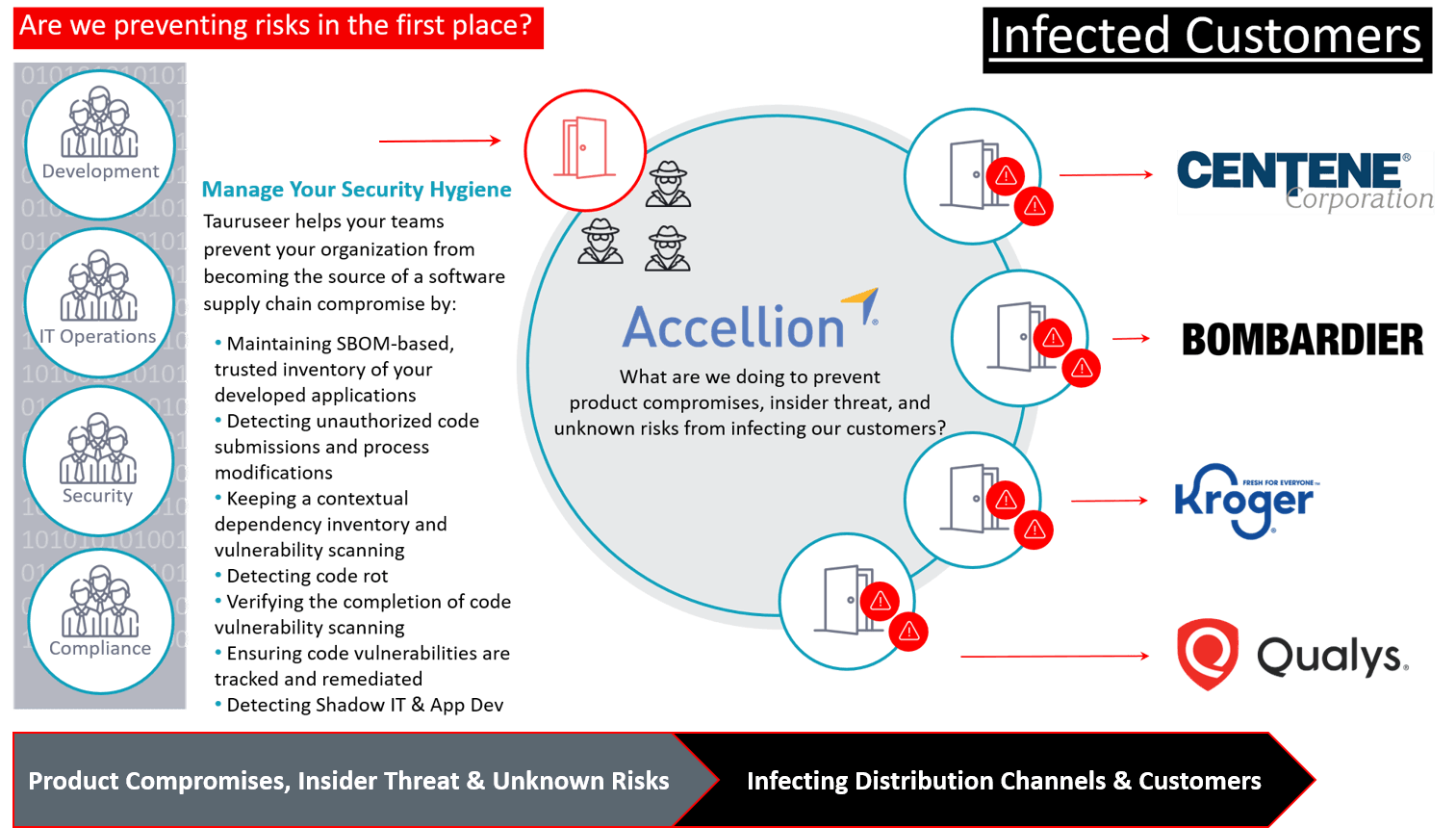
Then, only two months later, the Accellion attack — in which security firm
Accellion suffered a data breach due to adversaries exploiting four unpatched known vulnerabilities — serves as yet another urgent call to action.
FireEye Mandiant has covered the details of Accellion being used as the attack vector to breach several of its customers in the article,
Cyber Criminals Exploit Accellion FTA for Data Theft and Extortion, now affecting
healthcare insurer Centene as among the latest victims, which also includes security firm
Qualys,
Kroger, Bombardier,
Flagstar Bank, the Jones Day Law Firm, the Reserve Bank of New Zealand, the
Australian Securities and Investments Commission (ASIC), and
Transport for New South Wales (TfNSW).
The SolarWinds and Accellion software supply chain compromises have exposed the notion that without continuous assurance, “safety” is a fallacy, and everyone should acquire
evidence-based trust moving forward.
Traditionally, software supply chains referred to every code component involved in delivering a software product, from development to distribution channels, and everything in between.
Now in our digital world, everything is code and the risks are everywhere—SaaS, IoT, web, mobile, clouds—leaving existing security tools blind. The software supply chain is anything that touches that code from people, processes, and other technologies from build to runtime and maintenance with updates and enhancements (including new versions, exposed breach paths, DevOps tools, and security controls).
Even if the codebase is not touched for years, “Code Rot” naturally occurs over time which weakens software that was once “hardened.” While in parallel, hackers continuously find new ways to exploit the vulnerabilities they find within software and delivery processes.
They are doing this through
dependencies. This means that software supply chain risks are inherited in each organization from their software vendors, cloud solutions, and third-party code ecosystems.
If unchecked, dependencies leave organizations open to product compromises, insider threats, and exposed weaknesses. With organizations relying on thousands of software vendor suppliers, software supply chain security includes protecting all internally and externally sourced code, tools, and software products. This starts with gaining visibility and control over your entire organization and upholding your software vendor partners to new safety requirements.
Managing products is getting harder. And the way we work constantly changes with regulations and the adoption of new capabilities. But, we’re still spending time trying to answer questions with traditional approaches when security functions have moved to engineering.
Questions like: what threats and vulnerabilities do we have, who owns them, and are they putting customers at risk?
The Software Cybersecurity Assurance Challenge
Tauruseer solves one of the biggest and most fundamental problems DevOps, Security, and Compliance teams face today: software assurance for cybersecurity. Time is the enemy in product security, as the time with — new business requirements, manual code reviews, fixing bugs, tracking code and open source components in spreadsheets, smashing buttons on traditional AppSec tools to wait for days, and providing IT audit reports to constantly evolving regulations — when that time could be spent on innovating for, and protecting, their customers.
The Solution
Tauruseer solves the problem with a paradigm shift: by connecting to existing tools our customers already use that supports each DevSecOps product team (software, systems, and personnel), Tauruseer incorporates contextual controls within
NIST 800-53 to automate the correlation and analysis of risky scenarios to help customers with 3 things:
1. An always up-to-date, comprehensive Product Inventory
2. Enforcing a Culture of Safety
3. Automating Audit Ready All The Time
Once that is accomplished, Tauruseer can help customers
build trust with their enterprise customers through evidence-based risk management and actionable insight into their affected systems.
REAL Third-Party Risk Management: How Tauruseer Protects the Software Supply Chain
Security products claiming they can protect against third-party software supply chain compromise with network threat detection will have a hard time proving to be the silver bullet. Admittedly, every tool will have a hard time dealing with this problem. It is not a one and done approach and requires a comprehensive program with
platforms. Not just point solutions.
People still need to be directed to do the right work.
Executives and Senior Management still need the actionable context and insights to set the appropriate direction and monitor for improvements.
With Tauruseer, customers can lead their teams to put in the prioritized, proactive work that the
US's Cybersecurity & Infrastructure Security Agency (CISA) recommends
so you can prevent your organization from becoming the source of a supply chain compromise. By providing visibility and control, Tauruseer helps everyone—not just at the security engineer or developer-level—to see and keep track of risk management performance.
Both the software vendor and their customers are required to do work to protect the overall software supply chain ecosystem.
Let's look through the Tauruseer Solution's two perspectives:
- Accellion (vendor)
- Centene (customer)
Securing Critical Software Supply Chains
Modern software supply chains leverage DevSecOps environments and practices to accelerate the development and deployment of new capabilities. Tauruseer is the first platform to align and offer these new approaches out-of-the-box while applying additional security measures as recommended in
NIST SP 800-53,
validated by MITRE's report: "Deliver Uncompromised: Securing Critical Software Supply Chains."
Tauruseer identifies known breach paths, risky changes, and anomalies in software supply chains, including products and their supporting delivery processes leveraging DevOps and security management tools.
With a growing supply chain and more frequent software updates introduces new vulnerabilities to organizations, rapidly allowing attackers increased access to target networks. Tauruseer reveals any anomalous behavior or suspicious activity and identifies malicious intent or disengagement regarding code and security policies between DevSecOps teams.
Additionally, Tauruseer prevents unknown risks by helping organizations stay on top of all their code, including open source and third-party libraries, tied with their custom code, capturing details such as author and timestamp. Once mapped to a product centric context, Tauruseer automatically creates a trusted baseline, scans and updates automatically as trusted team members do their work.
Every time code changes by team members, Tauruseer creates a trusted software bill of materials (SBOM) baseline, including dependencies, contextual to every product. With automatic dependency vulnerability mapping and new code checks against code authors and trusted baselines (before the build system consumes it), Tauruseer provides investigation alerting of potential compromises, insecure fixes, or an assurance certification back to stakeholder dashboards.
Combined with code signing and container security tools, Tauruseer’s
Cognition Engine™ provides complete proactive risk intelligence coverage, offering correlations through the build and run processes so malicious activities or lack of risk performance will not go undetected.
Let us help your organization rethink how to secure critical software supply chains. Contact us and see how Tauruseer enables teams to proactively prevent code, products, and dependencies from constantly evolving software security hygiene risks.