(PART 2) FireEye & SolarWinds Breach: Continuous Assurance Explained & Why DevSecOps Is Not Enough
In Part 1 we helped with the understanding gap using this unfortunate, but recent, real-world example of a supply chain attack. Simply, this breach demonstrates the weakness in most software organizations we all rely on.
At Tauruseer, we take our science seriously and help our customers do the same. With a clear understanding of the challenges we all face, and with a shared framework to help us move forward, we can (and should) accelerate software ecosystems of risk posture maturity.
*Post updated 1/5/2021.
Tauruseer:
- video walkthrough of software ecosystem risks from April 2020
- introduce proactive concept like DevSecOps and while necessary, it is not sufficient
- propose Tauruseer's novel approach with out-of-the-box, automated use cases to detect and prevent future software supply chain attacks
In the wake of the SolarWinds breach, NIST's Ron Ross turns to DevSecOps approaches, where we must look at Agile & DevOps processes in an interview called, 'The Adversary Lives in the Cracks.' Ross calls attention to the fundamental need for better security across the entire software development lifecycle, stating the reality: "adversaries are exploiting bugs, weaknesses, and deficiencies in software to their advantage."
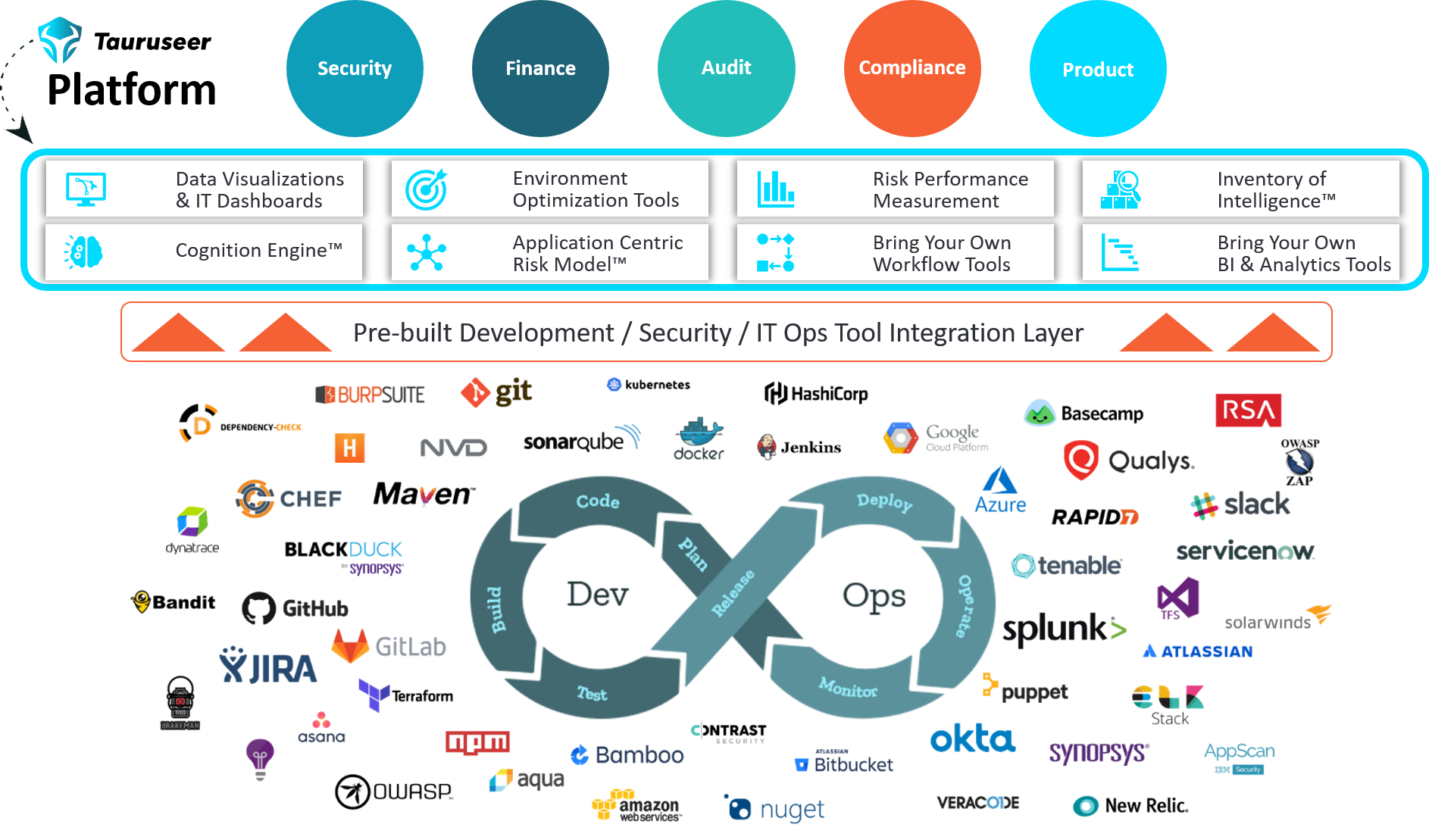
- A modern IT DevOps staff must be familiar with various technical tools, like:
cloud computing, containers, microservices, code repositories, continuous integration, continuous delivery, continuous deployment, and application performance monitoring.
- A modern IT DevSecOps staff must be familiar with various technical tools, like:
software component analysis (SCA )for open-source software components, dependency vulnerability mapping (DVM), static application security testing (SAST) for developers' code, container security scanning for container misconfigurations and vulnerabilities, and dynamic application security testing (DAST) for vulnerabilities within developed software.
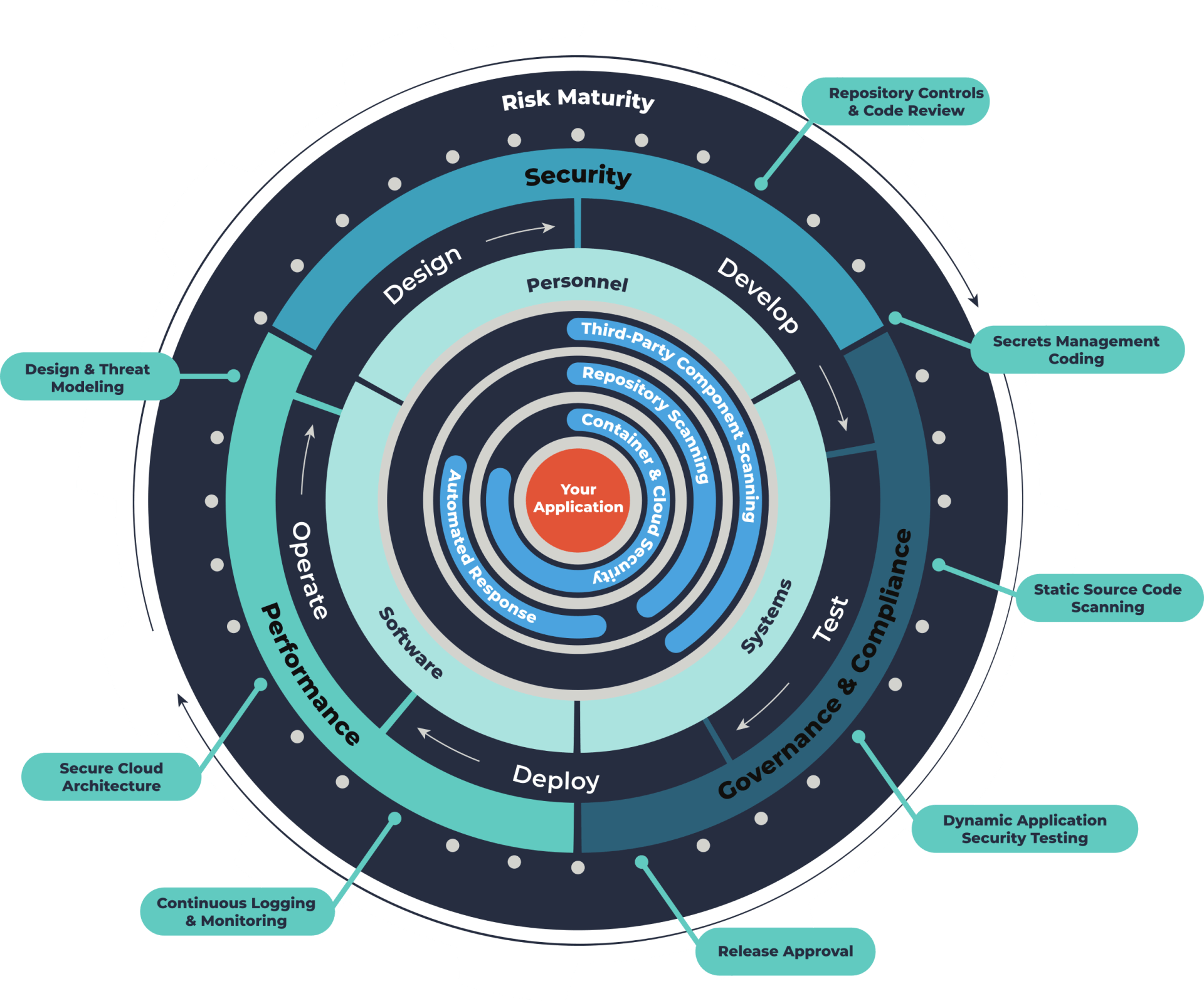
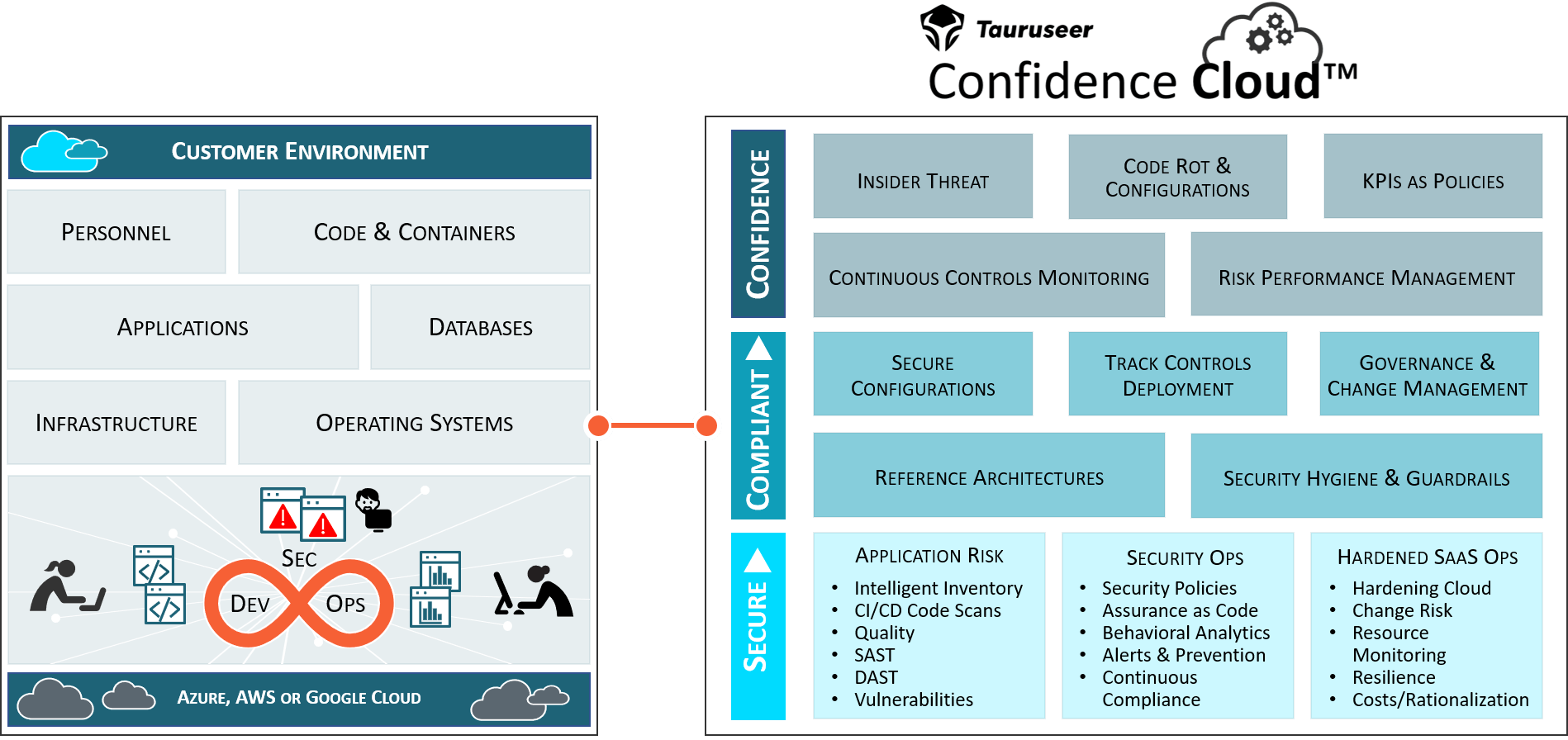
By now, most people realize this is a real wake-up call and a real opportunity. If a company wants to prevent malicious code injections, they must take steps to identify and monitor for the scenarios when this can happen. Tauruseer maintains the ability to automatically identify when a repository is out of governance, in this case a public repo, and when a non-team member has committed code.
- Cognition Engine™
— Tauruseer's proprietary correlation engine automates analytics with a growing list of pre-built "risky combinations" called "Cognitions." Cognitions pinpoint areas of change risk and illuminates actionable scenarios with prescriptive advice to prevent exploitation. Cognitions can also be predictive, automating data science techniques for visibility into potential future risks.
- Inventory of Intelligence™
— Tauruseer's proprietary entity configuration approach we call the Application Centric Risk Model™, simplifies complexity to contextualize and personalize high-priority risks for better communication, collaboration, and accountability.
- Environment Optimization Scorecard™ — Tauruseer's proprietary environment optimization tools continuously identifies adherence to best practices, regulatory compliance, and company policies to give management and senior leadership confidence security controls are adequately deployed, operating effectively, and proving continuous risk performance.
"Risky Combinations" and the cyber imperative
For those companies operating valuable business processes or producing products critical to their customers via software, this is your call-to-action to begin implementing proactive prevention measures via a platform-driven approach.
Either one of these alerts, if handled by a human, can prevent malicious code from going unnoticed and making its way into the distribution channels. But it is the historical tracking of "risky combinations" that could have further helped the teams see a threat pattern.
- In this context, an empowered IT DevSecOps organization leveraging the Tauruseer Continuous Assurance Platform could have:
1. Contextually baselined every application's supporting infrastructure, Bill of Materials, tool configurations, team members, certificates, risk performance metrics, and underlying dependencies
automatically checking for security violations with continuous feedback results for risky changes, prioritization, and remediation.
2. Detected malicious activity in any source control system for any code committed
that falls outside standard practices and security policies independent of any tool.
3.
Detected if an unauthorized individual has added code to a repository
across their entire application portfolio to determine if anyone was messing with their codebase and secretly installing backdoors or malware.
4. Detected any code repository change from private to public across their entire application portfolio to determine insecure misconfigurations, intent, and whether to revoke access control, and understand the potential business impact.
5.
Automatically mapped supply chain known vulnerabilities to every entity
so when an agency like NIST or The Cybersecurity and Infrastructure Security Agency (CISA)
releases an alert detailing active exploitations
with associated CVEs (CVE-2020-10148,
CVE-2020-14005, and
CVE-2020-13169) people can research and within minutes (rather than weeks or months) take action on
the right systems (your most critical risks).
Additionally, historical tracking of events in one platform enables our
Cognition Engine™ to alert when any
"risky combinations" like these are observed.
- Get code-to-cloud visibility and control of change risk across all of your operations
- Detect and mitigate security hygiene issues to reduce your attack surface
- Automate KPIs as policies in CI/CD pipelines to enforce risk posture across your full stack
- Stay audit ready for NIST, FedRAMP, CMMC, FISMA and other requirements
The Pentagon’s Cybersecurity Maturity Model Certification program starts next year. And, with the news of this exploited vulnerability in a commercial software product leading to a supply chain attack, achieving and keeping your Authority-to-Operate (ATO) is proving to be more critical than ever.
More news and blogs